Tag: fraud
What Is a Phishing Scam?

A phishing scam is a type of cybercrime in which criminals send emails or messages that appear to come from a legitimate source such as a bank, government agency, or payment processing service. They then use the email or message to persuade the recipient to disclose confidential information. This information can include account numbers, passwords, or credit card information.
This article will answer the following questions:
- How did “phishing scam” get its name?
- What are the five most common phishing scams?
- What is the intention of malicious software?
- What about ransomware?
- What types of businesses or organizations do phishing scams pose as?
- How can you tell a phishing scam from the real thing?
- How can I protect myself from a phishing scam?
How did “phishing scam” get its name?
The term “phishing” is a play on words and a variation of the word “fishing”. Fake emails, messages, and websites in a phishing scheme are used as lures to “fish” for personal or sensitive information.
What are the five most common phishing scams?
The five most common types of phishing scams include the following:
- Fake Websites. The scammers create a replica of a legitimate website that looks just like the real thing. They then use it to collect sensitive information including usernames and passwords in addition to credit card and banking information.
- Spear Phishing. The scammers send targeted fake emails to specific individuals or groups of people. The emails appear to come from a legitimate source such as a colleague or friend. The message will usually contain a link or attachment. When the link or attachment is accessed, it will download malicious software or take the user to a malicious website. The malicious software or website is then used to gain access to sensitive information or to install malware on the user’s computer.
- Malware. The scammers send malicious software or links to malicious websites that can infect a computer with viruses or steal personal information. They can also infect a computer with ransomware.
- Fake Updates. They send fake software updates or security patches that appear to be from a legitimate source but are actually malicious software.
- SMS Phishing (Smishing). They send text messages to individuals that appear to come from a legitimate source. The messages, in turn, contain malicious links.
What is the intention of malicious software?
The intention of malicious software, also known as malware, is to damage, disrupt, or gain unauthorized access to a computer system or network. Malware is typically designed to perform one or more of the following activities: steal data, monitor user activity, deliver spam and malicious links, launch denial-of service attacks, or even take control of a system. A Denial of Service (DoS) attack prevents legitimate users from accessing a target service or system. This is typically accomplished by flooding the targeted service or system with a large amount of traffic or requests. This causes the service or system to become overloaded and unresponsive. DoS attacks can be used to cause a service or system to become temporarily unavailable or to cause a permanent denial of service.
Once on a system, malware can collect and transmit sensitive data to the attacker. This can include passwords, financial information, and other confidential information. Additionally, malware can be used to create a backdoor, which allows the attacker unauthorized access to the system and data.
What about ransomware?
Another type of malicious software that is the goal of attackers is ransomware. Ransomware is designed to block access to a computer system or its data until a ransom is paid. In some cases, ransomware will display a message to inform the user of the encryption placed on their system and then to demand payment for the decryption key. In addition to malicious attachments or links to malicious websites in phishing emails, ransomware can also be spread through vulnerable networks such as those with weak passwords or outdated software. Ransomware can be extremely damaging to individuals and organizations, as it can prevent victims from accessing their data and systems until the random is paid. In some cases, ransomware can even spread to other devices if they are connected to the same network.
What types of businesses or organizations do phishing scams pose as?
Phishing scams can pose as many types of legitimate businesses, but some businesses and organizations are used more than others:
- Banks/Financial Institutions. Phishers often pose as banks or other financial institutions to attempt to acquire access to personal information about users. They may send emails or text messages asking for verification of sensitive information such as credit card numbers, bank account numbers, passwords, and Social Security numbers.
- Government Agencies. Phishers also pose as government agencies such as the IRS or Social Security Administration. These messages appear to come from government sources but are fake. Their goal is to get users to provide personal information such as Social Security numbers or to pay money.
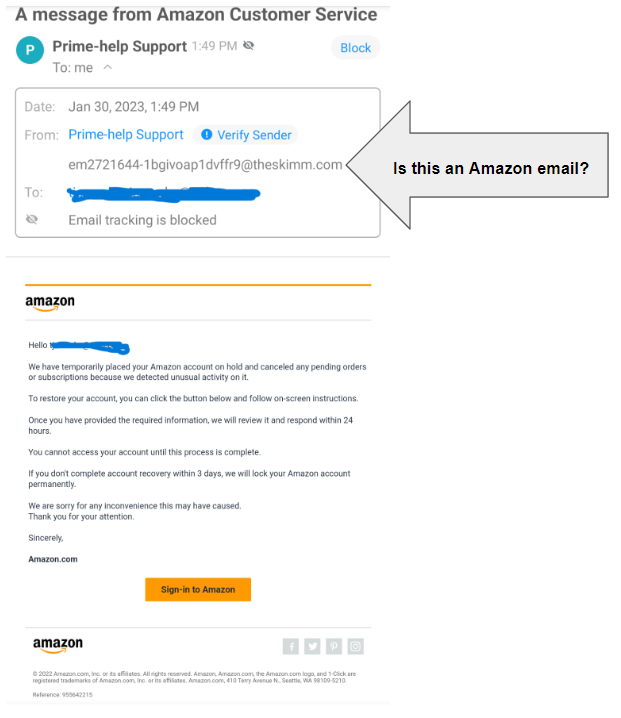
- Online Retailers. Phishers pose as online retailers such as Amazon or eBay to get users to provide personal information or credit card numbers. These messages may look like official emails from the particular retailer or may be sent through phishing websites.
- Social Networking Websites. Phishers sometimes pose as social networking websites such as Facebook or Twitter to get users to provide personal information or to click on malicious links. These messages may contain false promises of free gifts, discounts, or access to exclusive content.
- Payment Processing Services: Phishers may pose as payment processing services such as PayPal or Venmo to get users to provide personal information or credit card numbers. These messages may also look like official emails or may be sent through phishing websites.
How can you tell a phishing scams from the real thing?
The intention of malicious software, also known as malware, is to damage, disrupt, or gain unauthorized access to a computer system or network. Malware is typically designed to perform one or more of the following activities: steal data, monitor user activity, deliver spam and malicious links, launch denial-of service attacks, or even take control of a system. A Denial of Service (DoS) attack prevents legitimate users from accessing a target service or system. This is typically accomplished by flooding the targeted service or system with a large amount of traffic or requests. This causes the service or system to become overloaded and unresponsive. DoS attacks can be used to cause a service or system to become temporarily unavailable or to cause a permanent denial of service.
Once on a system, malware can collect and transmit sensitive data to the attacker. This can include passwords, financial information, and other confidential information. Additionally, malware can be used to create a backdoor, which allows the attacker unauthorized access to the system and data.
How can I protect myself from phishing scams?
There are several steps you can take to protect yourself from a phishing scam:
- Set your email to show a preview. If an email looks suspicious, don’t even open it.
- Be suspicious of unsolicited emails, even from people you know. If an email seems suspicious in any way, don’t click on links or open attachments.
- Be wary of emails that include misspellings or poor grammar.
- Instead of responding to suspicious emails, call or contact the business or organization in question on your own.
- Don’t respond to emails that ask for your username, password, or other sensitive information. A legitimate company will not ask for that type of information via email.
- Pay attention to the URL of a website. If it looks suspicious, don’t enter info on the site.
- Check your bank and credit card statements regularly for unauthorized charges.
- Use anti-virus and anti-malware software to protect your computer from malicious software.
- When available, use two factor verification.
Matraex is a software and app development company based in Boise, Idaho. We would like to help you with all of your app development and technology concerns. Feel free to contact us, leave a question on our instant messaging feature on our website, or send us a question through our Google Business profile. We look forward to answering your questions.
Sign up to receive answers to your questions delivered directly to your inbox!
