Category: You Asked, We Answered
What Three Countries Have the most App Developers?

The top three countries with the most app developers include the United States, India, and China. Other countries with a large amount of app developers include the United Kingdom, Brazil, Russia, Canada, and Germany. The exact number of developers in each country is unknown and appears to be in a constant state of flux, but the info provided here is the most accurate that can currently be found.
The United States
As of February, 2023, the United States reportedly has more app developers than any other country, with somewhere between 3 and 5 million by most accounts, but some numbers reported as high as six million. The U.S. is known for creating a wide range of different apps. These apps include gaming, productivity, finance, and health and lifestyle apps, with many of the apps focused around the consumer. There are also many app development companies that create business apps in the United States including Salesforce, Oracle, and Zendesk. Popular apps that originated in the United States include the following:
- Instagram: a popular social media platform.
- Snapchat: a popular social media platform for sharing personal videos and pictures.
- Uber: used to get rides and items delivered.
- WhatsApp: a popular communication platform that allows you to call or text anywhere.
- Netflix: a popular video stream platform.
- Pinterest: a social media platform for sharing and selling items through memes and pictures.
India
India is #2 for the amount of app developers. The exact number is all over the place, but there appears to be over 3 million. There is a definite chance that India will overtake the United States in the next few years with its number of app developers. Mobile banking, lifestyle, travel, social media, and eCommerce apps are the most popular apps built in India. Popular Indian apps include the following:
China
China is listed as having the third highest number of app developers, though it may actually be higher. Once again, the numbers are everywhere with anywhere from 2 million to 8 million developers is a possibility, and China greatly surpassing the rest of the world in the amount of people who use apps. China has over 989 million internet users out of its population of 1.4 billion. China also exports more software than any other country. Messaging, gaming, and entertainment apps are the most popular apps developed in China. Several of the most popular apps developed in China include
- WeChat: an instant messaging, social media, and mobile payment app. It became the world’s largest standalone mobile app in 2018, with over 1 billion subscribers.
- TikTok: a platform in which users download and share short, personalized videos
- Pinduoduo: an eCommerce platform that connects farmers and those in the agriculture industry directly with consumers.
- Alibaba: an eCommerce platform that allows buying, selling, manufacturing, and personalizing of products.
Matraex is a premier app and software development company located in Boise, Idaho, and we would like to answer any software development or technology questions that you might have to help you become a more informed consumer. Contact us, message us through the feature on our website, or post a question on our Google business profile page. We look forward to answering your questions.
Sign up to receive answers to your questions delivered directly to your inbox!
What Is an IP Address?

An IP address (Internet Protocol address) is a numerical label assigned to each device that is connected to a computer network that uses internet protocols for communication. These devices can include computers, printers, and mobile devices. If a device uses the internet to communicate, it must use internet protocols. An IP address is used to identify and locate the device on the network so information can be sent to and from that particular device. It also provides the physical location of the device. IP addresses are typically written as a series of four numbers with each series separated by a period. For example, an IP address might look like this: 192.168.1.1.
IP addresses are essential for the internet to operate. They allow devices to identify and communicate with each other.
Questions answered in this article include the following:
What can you learn by knowing an IP address?
By knowing an IP address of a device, you can learn the following information:
- The geographic location of a device. Most IP address formats allow you to determine the country, region, and city a device is located in. For example, IP addresses from the United States generally begin with “192.” “172.16”, or “10”.
- The type of network a device is connected to. Using the above example, “192” is reserved for small networks, “172” is reserved for medium-sized networks, and “10” is designed for large networks.
- The type of device. Certain IP address formats can help you identify the type of device, though you may not be able to determine that info from the IP address alone and more information might be needed. Those devices can include computers, routers, or servers to name a few.
- The owner of the device. An IP address can help you identify the whether the owner of the device is an individual or a business entity. It may also give you clues on who the owner is, though that information is difficult to ascertain.
- The operating system and software installed on the device. Certain IP address formats can help you determine the type of operating system and the software installed on the device.
Does the IP address of a device change when its physical location changes?
The IP address of a device does usually change when its physical location changes. When a device is connected to the internet, it is assigned a unique IP address by the Internet Service Provider (ISP). If the device is moved to a new physical location, it will be assigned a new IP address by the new ISP or by the existing ISP if the ISP doesn’t change. The IP address changes because the ISP needs to be able to track the device’s location to provide the best service.
As for cell phones and other mobile devices, an IP address is assigned to a mobile device by the cellular service when the phone is connected to their network. Mobile phones have dynamic IP addresses. This means that a new IP address is assigned each time the phone connects to the network from a different location. This allows the network to keep track of the device as it moves to different locations. Adversely, it does make it much more difficult to track a mobile phone through an IP address.
How do businesses use IP addresses?
Businesses use IP addresses for a number of purposes. They use them to identify and connect to computers, printers, and other devices on their networks. They also use IP addresses to connect with external networks including the internet. Businesses may also use IP addresses to restrict access to their networks, such as a user who is accessing their website from a different computer for the first time. Because businesses can use IP addresses to restrict access, they can also protect their systems against malicious activity such as viruses. This is done by allowing networks to filter out traffic from unwanted sources.
IP addresses also allow businesses to track usage and trends. These trends might include to determine where they are getting most of their traffic from, to see frequent visitors, and to track specific visitors to see their visits to the business’s website and app prior to making a sale.
Since IP addresses identify a user’s location, they can also be used by businesses to provide location-based services such as specialized advertising. In this manner, they can target their advertising efforts to specific geographic areas. This can help them to save money on advertising and to ensure that their ads are seen by the most relevant audience.
Businesses can also use IP addresses to implement network security measures such as firewalls. Firewalls are implemented by allowing only certain IP addresses to visit a site or by tracking down and blocking IP addresses of malicious actors.
How can IP addresses be used to commit cyber attacks?
IP addresses can be used in a number of ways to commit cyber attacks. Two of the most common ways include a distributed denial-of-service (DDoS) attack, a man-in-the-middle attack or through port scanning:
DDoS Attack: In a DDoS attack, a malicious actor sends a large amount of traffic to a targeted IP address. The goal is to overwhelm the system and make it unavailable for legitimate users. In a DDoS attack, the attacker can use automated tools to generate requests from multiple IP addresses to make the attack difficult to detect and the perpetrator difficult to locate.
Man-in-the-Middle Attack: In a man-in-the-middle attack, the attacker intercepts communications between two IP addresses to an IP address that they control. By doing so, the attacker can monitor or modify the data as it passes from one user to another to possibly gain access to sensitive information from either party
A third way that cyber criminals can gain access to information is through port scanning. Port scanning involves sending data to a targeted system to determine what ports on the system are open, closed, or filtered in some way. This is often used by cyber criminals to identify potential targets and by security professionals to identify potential weaknesses of a system.
Can an IP address be hidden?
An IP address can be hidden by using a Virtual Private Network (VPN). A VPN uses encryption and authentication technologies to ensure that the data being sent over a public network is secure which can prevent cyber attacks. VPNs are commonly used to securely access and share data over a public network as though the device was connected to a private network. These public networks can include anywhere that provides public internet access including coffee shops and libraries. VPNs are frequently used by remote workers.
VPNs are also used to bypass geographic restrictions and censorship. This allows users to access websites and services that may be blocked in their country. This can be a useful tool for journalists, activists, and other individuals who may need access to information that is otherwise restricted.
The problem with VPNs is that they can also be used for cyber attacks. When using a VPN, an attacker would remain anonymous throughout an attack.
Matraex is a premier app and software development company located in Boise, Idaho. Do you have any questions regarding app development or any of today’s computer technology? Matraex would like to be your go-to source for unbiased answers. Contact us, leave a message on the live chat feature on our website, or place a question on our Google Business Profile page. We look forward to answering all of your tech questions so you can be an informed consumer.
Sign up to receive answers to your questions delivered directly to your inbox!
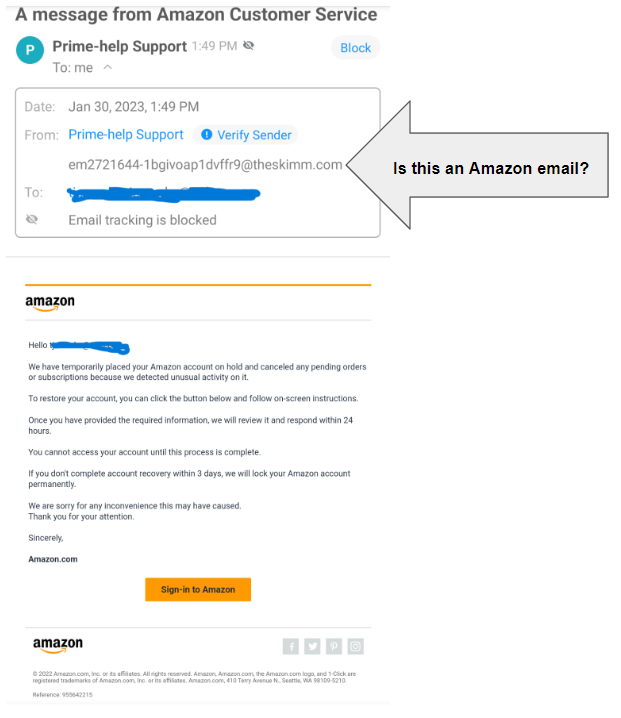
What Is a Phishing Scam?

A phishing scam is a type of cybercrime in which criminals send emails or messages that appear to come from a legitimate source such as a bank, government agency, or payment processing service. They then use the email or message to persuade the recipient to disclose confidential information. This information can include account numbers, passwords, or credit card information.
This article will answer the following questions:
- How did “phishing scam” get its name?
- What are the five most common phishing scams?
- What is the intention of malicious software?
- What about ransomware?
- What types of businesses or organizations do phishing scams pose as?
- How can you tell a phishing scam from the real thing?
- How can I protect myself from a phishing scam?
How did “phishing scam” get its name?
The term “phishing” is a play on words and a variation of the word “fishing”. Fake emails, messages, and websites in a phishing scheme are used as lures to “fish” for personal or sensitive information.
What are the five most common phishing scams?
The five most common types of phishing scams include the following:
- Fake Websites. The scammers create a replica of a legitimate website that looks just like the real thing. They then use it to collect sensitive information including usernames and passwords in addition to credit card and banking information.
- Spear Phishing. The scammers send targeted fake emails to specific individuals or groups of people. The emails appear to come from a legitimate source such as a colleague or friend. The message will usually contain a link or attachment. When the link or attachment is accessed, it will download malicious software or take the user to a malicious website. The malicious software or website is then used to gain access to sensitive information or to install malware on the user’s computer.
- Malware. The scammers send malicious software or links to malicious websites that can infect a computer with viruses or steal personal information. They can also infect a computer with ransomware.
- Fake Updates. They send fake software updates or security patches that appear to be from a legitimate source but are actually malicious software.
- SMS Phishing (Smishing). They send text messages to individuals that appear to come from a legitimate source. The messages, in turn, contain malicious links.
What is the intention of malicious software?
The intention of malicious software, also known as malware, is to damage, disrupt, or gain unauthorized access to a computer system or network. Malware is typically designed to perform one or more of the following activities: steal data, monitor user activity, deliver spam and malicious links, launch denial-of service attacks, or even take control of a system. A Denial of Service (DoS) attack prevents legitimate users from accessing a target service or system. This is typically accomplished by flooding the targeted service or system with a large amount of traffic or requests. This causes the service or system to become overloaded and unresponsive. DoS attacks can be used to cause a service or system to become temporarily unavailable or to cause a permanent denial of service.
Once on a system, malware can collect and transmit sensitive data to the attacker. This can include passwords, financial information, and other confidential information. Additionally, malware can be used to create a backdoor, which allows the attacker unauthorized access to the system and data.
What about ransomware?
Another type of malicious software that is the goal of attackers is ransomware. Ransomware is designed to block access to a computer system or its data until a ransom is paid. In some cases, ransomware will display a message to inform the user of the encryption placed on their system and then to demand payment for the decryption key. In addition to malicious attachments or links to malicious websites in phishing emails, ransomware can also be spread through vulnerable networks such as those with weak passwords or outdated software. Ransomware can be extremely damaging to individuals and organizations, as it can prevent victims from accessing their data and systems until the random is paid. In some cases, ransomware can even spread to other devices if they are connected to the same network.
What types of businesses or organizations do phishing scams pose as?
Phishing scams can pose as many types of legitimate businesses, but some businesses and organizations are used more than others:
- Banks/Financial Institutions. Phishers often pose as banks or other financial institutions to attempt to acquire access to personal information about users. They may send emails or text messages asking for verification of sensitive information such as credit card numbers, bank account numbers, passwords, and Social Security numbers.
- Government Agencies. Phishers also pose as government agencies such as the IRS or Social Security Administration. These messages appear to come from government sources but are fake. Their goal is to get users to provide personal information such as Social Security numbers or to pay money.
- Online Retailers. Phishers pose as online retailers such as Amazon or eBay to get users to provide personal information or credit card numbers. These messages may look like official emails from the particular retailer or may be sent through phishing websites.
- Social Networking Websites. Phishers sometimes pose as social networking websites such as Facebook or Twitter to get users to provide personal information or to click on malicious links. These messages may contain false promises of free gifts, discounts, or access to exclusive content.
- Payment Processing Services: Phishers may pose as payment processing services such as PayPal or Venmo to get users to provide personal information or credit card numbers. These messages may also look like official emails or may be sent through phishing websites.
How can you tell a phishing scams from the real thing?
The intention of malicious software, also known as malware, is to damage, disrupt, or gain unauthorized access to a computer system or network. Malware is typically designed to perform one or more of the following activities: steal data, monitor user activity, deliver spam and malicious links, launch denial-of service attacks, or even take control of a system. A Denial of Service (DoS) attack prevents legitimate users from accessing a target service or system. This is typically accomplished by flooding the targeted service or system with a large amount of traffic or requests. This causes the service or system to become overloaded and unresponsive. DoS attacks can be used to cause a service or system to become temporarily unavailable or to cause a permanent denial of service.
Once on a system, malware can collect and transmit sensitive data to the attacker. This can include passwords, financial information, and other confidential information. Additionally, malware can be used to create a backdoor, which allows the attacker unauthorized access to the system and data.
How can I protect myself from phishing scams?
There are several steps you can take to protect yourself from a phishing scam:
- Set your email to show a preview. If an email looks suspicious, don’t even open it.
- Be suspicious of unsolicited emails, even from people you know. If an email seems suspicious in any way, don’t click on links or open attachments.
- Be wary of emails that include misspellings or poor grammar.
- Instead of responding to suspicious emails, call or contact the business or organization in question on your own.
- Don’t respond to emails that ask for your username, password, or other sensitive information. A legitimate company will not ask for that type of information via email.
- Pay attention to the URL of a website. If it looks suspicious, don’t enter info on the site.
- Check your bank and credit card statements regularly for unauthorized charges.
- Use anti-virus and anti-malware software to protect your computer from malicious software.
- When available, use two factor verification.
Matraex is a software and app development company based in Boise, Idaho. We would like to help you with all of your app development and technology concerns. Feel free to contact us, leave a question on our instant messaging feature on our website, or send us a question through our Google Business profile. We look forward to answering your questions.
Sign up to receive answers to your questions delivered directly to your inbox!
As an App Founder, What Do I Need to Know about Passwords?
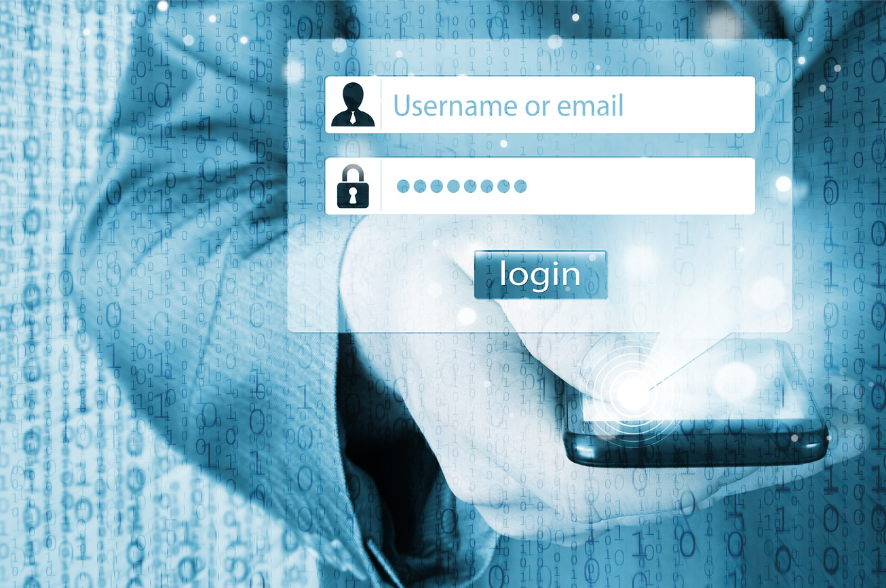
Passwords are an essential part of any application or website security system and one of the most important security measures they can take to protect their app. They provide a layer of protection that prevents unauthorized access to your software and its data. Passwords also help to protect user data from being accessed by the wrong people. This can include credit card information, addresses, and other private information that could lead to malicious activity including identity theft. Furthermore, passwords are a way to validate user identity to tools and services such as your SMTP Credentials on AWS SES, and to ensure that only authorized users can access an application and its data. Hence, the best passwords should be strong, unique, and regularly changed.
In this article, we will answer the following questions:
- How long and difficult should a password be?
- How often is it recommended that users change passwords?
- What types of businesses require a higher level of password security?
- What features can be added to my app to increase password security?
- What are negative consequences for setting password standards too low for my website or app?
How long and difficult should a password be?
The longer and more intricate a password is, the harder it will be to figure out and subsequently break into a system. The following are commonly recommended guidelines regarding length and complexity of passwords and includes some practices that will also keep your passwords safe:
- Create passwords that are at least 8 characters long. Ideally, a password should be 12 characters or more.
- Use a combination of upper and lower case letters, numbers, and special characters.
- Avoid using personal information in passwords. That includes names, birthdates, or addresses.
- Avoid using common words, phrases, or sequences, as they can easily be guessed.
- Avoid using the same password for multiple accounts.
- Use a different, unique password for each online account and app. This will prevent unauthorized access to multiple accounts if one password is compromised.
- Don’t write down your passwords.
- Use a password manager for secure storage of complex passwords.
More characters, capital letters, numbers, and a special character or two can greatly increase the difficulty related to determining what a password is. Below is a chart showing exactly how longer and more intricate passwords greatly increase the amount of time it will take a computer to figure out a password.
How often is it recommended that users change passwords?
Passwords should be regularly changed, especially after major changes or updates to a website or app. It is also frequently recommended that passwords be changed every 3-6 months. Some businesses that deal with sensitive information and a number of government agencies require numbers to be changed every 30 days. Why? Passwords can be exposed over time, either through malicious activities or because of password reuse. By changing passwords, it ensures that if passwords were obtained, the person who acquired it cannot use it for any extended amount of time. Also, if passwords are reused on multiple accounts, changing the password regularly helps to ensure that if one account is compromised, other accounts are not also at risk.
What types of businesses require a higher level of password security?
While all businesses, organizations, and institutions should be concerned with password security, some are obviously at more risk for breaches than others:
- Banks and financial institutions. They store and manage customers’ financial information including credit card and Social Security numbers. Therefore, strong password security is essential to protect against data breaches and unauthorized access to this sensitive info.
- Health apps. They often store highly sensitive medical information including medical records, insurance information, and prescription information. In addition, they are subject to the HIPAA law that states that no sensitive patient info can be disclosed without the patient’s consent or knowledge. Strong password security is necessary to ensure that information is kept confidential and to protect against potential data breaches.
- Retailers. Online businesses often retain their customers’ personal information. This information includes credit card numbers, home addresses, and phone numbers. Strong password security is necessary to protect the information from unauthorized access and potential data breaches.
- Government Agencies. Such entities often store and manage sensitive information including national security information, tax records, and other confidential information. Strong password security is needed to protect against unauthorized access to the information and data breaches.
What features can be added to my app to increase password security?
An app founder has many options to choose from to increase their app’s security:
- Requiring a minimum password length. This is done by setting a minimum character limit to passwords.
- Requiring a combination of letters, numbers, and symbols in a password.
- Requiring users to change their password every 3-6 months, possibly more regularly depending on the nature of the business.
- Two-factor authentication. This adds a second layer of security, such as a code sent to a user’s email or phone. It helps to ensure that only the intended user gains access to an account. It also prevents hackers from accessing an account, even if they have obtained the user’s password.
- Allowing users to utilize a password manager. This helps users generate strong, unique passwords that are unique for each of their accounts. It also helps to prevent users from using weak and easily guessable passwords that can easily be cracked.
- Logging failed password attempts and locking out users after a certain number of failed attempts.
- Adding Captchas to login requirements. A Captcha is a challenge response test that is required as part of the login process. This helps to make certain that the one logging in is human.
- Requiring one-time passwords when registering with an app. One-time passwords are temporary passwords that are only valid for a single use and are used to authenticate users on websites or applications.
- Adding biometric authentication. Biometric authentication uses a user’s physical characteristics such as fingerprints or voice recognition to verify their identity.
An app founder may want to discuss the different features that will increase app security with their app developer to determine what features would make sense for their app.
What are negative consequences of setting password standards too low for my website or app?
When you choose low standards for passwords on your website or app, you or your users may encounter a number of negative consequences:
- You and your users are at an increased security risk because you make it easier for hackers to guess passwords and to gain access to accounts. This could potentially lead to a security breach, which would put the website or app at risk of having user data exposed or stolen. It can also result in identity theft and financial loss for the app’s users.
- It may create a false sense of security for the app’s users. If users are allowed to set weak passwords, they may believe that their account is secure when, in reality, they are vulnerable to attack.
- It can lead to a poor user experience. Weak passwords are often easy to remember, but it could also lead to users forgetting their passwords or having to reset them frequently. This can result in frustration and a decreased desire to use the app.
- If a website or app has weak password standards, it could lead to a loss of reputation. This can be damaging to the brand, as users may be less likely to trust the website or app if they know their data is not secure.
- If a website or app does not adhere to the industry standards for password strength, it could be subject to fines or other penalties from regulatory authorities. This could be especially damaging for businesses or organizations that rely of their website or app for their operations and income.
Matraex is a premier app developer located in Boise, Idaho. Do you have a question about app development? Matraex would like to be your go-to place for answers. You can leave us a question on our Google Business Profile, contact us through our website, or leave a question via our chat feature on the website. Let us help you become more informed so you can make decisions that will best suit you.
Sign up to receive answers to your questions delivered directly to your inbox!
What is SaaS Software?

A SaaS, “Software as a Service,” application is a type of cloud computing application that is hosted by a third-party provider and is made available to customers over the internet. SaaS software and apps typically provide customers with business applications which are delivered on a subscription basis. Customers then pay a set fee on a regular basis, usually monthly or yearly, to access the application. Many SaaS apps offer free versions of the software that can be upgraded for more functionality. Many also offer a free or inexpensive trials of the software so users can determine if the app suits their needs prior to committing to a paid plan.
Questions answered in this article include the following:
What are the advantages of using SaaS software?
Incorporating SaaS apps into a business often has many advantages:
- Flexibility: SaaS applications are often highly scalable and can be customized easily to meet the changing needs of a business.
- Ease of Use: SaaS applications are usually easy to set up and use. This allows a business to start using them quickly with minimal effort.
- Automation: SaaS applications automate many manual processes. This saves businesses time and money.
- Accessibility: Saas applications are typically accessible from any device with an internet connection so users can access them from anywhere that has such a connection.
What are the disadvantages of using SaaS software?
SaaS software also has a number of disadvantages:
- Limited Control: Unlike traditional software, with SaaS apps, the user can only access and configure the application as much as the provider allows and cannot customize it beyond that point.
- Inability to Integrate: A business may not be able to integrate SaaS applications with their existing applications and systems. This is particularly true if a business needs to access data from multiple sources.
- Reliability: SaaS software can be unreliable because it is not accessible if the SaaS provider or the internet connection goes down.
- Expense: While most SaaS solutions are affordable, they are mostly subscription-based, so business can end up paying more than intended with multiple subscriptions. When utilizing SaaS software, it may be important to keep track of expenses so they don’t get out of hand.
Is SaaS software a good option for my business?
It depends. It can be, but it depends on the parameters of the business. SaaS software can be very cost effective for many businesses because the business does not need to purchase, install, and maintain the software themselves. If the business requires multiple users to access the application, however, it can potentially become very expensive. Also, since security is maintained by the host company who regularly monitors and updates the software, it tends to be very secure. It is hosted on the cloud, however, which tends to reduce security. In addition, if a business needs a lot of control over the software beyond what a provider allows or if they need to integrate many systems, SaaS software may not be the best solution. Whether SaaS software will be a good option for a business depends on their needs. Before choosing SaaS software, a business must evaluate its needs and whether SaaS software can meet those needs. Only they can decide if SaaS software will work for them.
What are the most common problems Saas software solves?
Below is a list of common problems that SaaS software can help with in addition to a few popular SaaS software solutions a business owner could possibly look into for each problem. This subject will be covered more in-depth with more specific SaaS solutions a business could consider in a future blog.
Collaboration
Businesses have used collaboration tools for a while, but with the onset of Covid and the need to collaborate away from the office, it became essential for teams to effectively work together without being in the same physical space. Google Drive and Dropbox both offer cloud-based file storage and collaboration solutions. Google Drive provides users with real-time, often free, collaboration with shared documents, spreadsheets, and presentations. They also offer a suite of office tools including Google Docs, Sheets, and Slides. Dropbox, on the other hand, provides users with secure file storage, online sharing, and synchronization capabilities.
File Sharing
In conjunction with collaboration, teams often need a way to share files, not only amongst themselves but also with others outside of the team including clients in some cases. Google Drive and Dropbox come to the rescue again with cloud-based file storage and sharing solutions. Google Drive allows users to securely share files with anyone and to control access the their files. Dropbox also enables users to share files quickly and securely.
Project Management
Business teams often need a way to manage projects which are being worked on by multiple members of a team. They need to keep track of who is doing what for a particular project and where in the process the project is. Asana and Trello both offer project management solutions. Asana is a project management platform that helps teams organize and track projects, tasks, and conversations. Trello enables users to create collaborative boards, lists, and cards to help manage and track projects.
Customer Relationship Management (CRM)
Those in sales often have many contacts. In addition, they need to keep track of when to contact who, what was said, and who is in what stage of a sale. In addition, they need to constantly add to that contact list. There’s many components to juggle, and dropping the ball could mean losing a sale. Salesforce and Zoho offer SaaS CRM solutions. Salesforce is a cloud-based platform that helps sales teams manage customer data and relationships. Zoho offers businesses a suite of CRM tools that enable them to manage contacts, customer support, and sales activities.
Analytics
Tracking analytics has become an important part of business. Businesses today need to track how their website is performing and what is converting viewers into customers so they can take advantage of what is working. Analytics are also used by businesses to determine what needs to be changed or tweaked to help businesses grow. Google Analytics and Mixpanel both offer analytics solutions. Google Analytics helps businesses track and analyze website performance metrics such as page views, visitor behavior, and conversions. Mixpanel provides real-time insights into user behavior and engagement.
Email Marketing
Many businesses need a convenient way to keep track of email contacts and put them into groups as well as automate email and newsletter campaigns. In addition, they need to track how well their campaigns do so they can modify their attempts going forward. Mailchimp and Constant Contact both offer SaaS email marketing solutions. Mailchimp helps business manage and automate email campaigns and provides analytics on the campaigns. Constant Contact provides users with customizable email templates and a suite of tools to help business create, send, and track email campaigns.
Online Payments
Online businesses, regardless of whether they supply goods or services, often need a convenient, secure, and reliable way to take payments online. PayPal and Stripe are examples of SaaS software that provides users with ways to both send and receive money, process payments online, and keep track of sales received. They also provide tax documents of income when needed.
Video Conferencing
Covid also made many businesses rethink and come up with alternatives to in-person meetings. They couldn’t happen during the height of the pandemic, and no one knew how long it would be before things would return to “normal”. Hence, video conferencing, which existed prior to Covid, became an essential business tool and has continued to be in wide use ever since. Zoom and Skype offer SaaS video conferencing solutions. They both provide users with high-quality video, audio, and text chat in addition to screen sharing and recording capability.
Document Automation
Businesses needed a way to not only share documents but to allow other parties to sign documents in a secure way that would be legally binding for customers and clients, as well as for onboarding/offboarding employees. DocuSign and HelloSign offer document automation solutions. They both enable businesses to securely send, sign, and manage documents including important contracts.
Human Resources
Businesses often do not have the means to hire a full-time, dedicated HR specialist, but SaaS HR solutions have automated the process for many businesses. Two such programs are BambooHR and Workday. BambooHR helps businesses manage employee data and automate HR processes. Workday provides users with a unified platform to manage payroll, time and attendance, talent, and performance reviews.
Matraex is a custom app development company based in Boise, Idaho, and we would like to be your go-to source for answers to your app development and technology questions. Feel free to contact us, leave a note on our website’s instant messaging feature, or leave us a question on our Google Business Profile. We look forward to hearing from you.
Sign up to receive answers to your questions delivered directly to your inbox!
What Is a Responsive Website?

A responsive website is a website that is designed to respond to the user’s behavior and environment based on the screen size, platform (desktop monitor, tablet, phone and so on), and orientation (whether portrait or landscape) of the device they are using. A responsive website uses fluid, proportion-based grids and flexible images to create a dynamic, flexible website that provides a great user experience that looks great on any device.
Questions that will in answered in this article include the following”
- Why is it important to have a responsive website?
- What are the negative consequences of not having a responsive business website?
- What are some common misconceptions about responsive websites?
- How can I tell if my website is responsive?
- If I am using a website builder, do I need to worry about my website being responsive?
- How do I make my website responsive?
Why is it important to have a responsive website?
Websites are viewed in many different ways and on many different devices. Long gone are the days of a website being viewed on a desktop monitor most of the time. The platforms used to access a website depends on the target audience and the content of the website, but the trend for many years has leaned heavily towards mobile devices. According to Oberlo, just ten years ago, over 90% of website traffic occurred on desktop computers. By late 2022, those figures had totally changed. Now, over 60% of all web traffic comes through mobile devices, with over 50% of all website visits coming through such devices.
In addition, more and more people are accessing websites through other internet-capable devices. These devices include wearable devices and their car’s navigation systems among other platforms. It is important that your website can be viewed properly regardless of the device that is being used because it allows users to have a better user experience, and the better the experience, the more likely they will spend more time visiting and interacting with the website. Google also rewards websites that are optimized for mobile devices by ranking them higher in search engine results, so having a responsive website is also important for SEO.
What are the negative consequences of not having a responsive business website?
There are a number of potential negative consequences of a website not being responsive.
- Loss of Traffic: Without a responsive website, some users may find it difficult to access the website on their mobile devices. This could lead to a decrease in website visits. Customers may also be unable to find what they’re searching for on the site.
- Poor User Experience: Since the content and design may not be displayed correctly on mobile devices, users may have a poor experience. This could cause customers to leave the website and not return.
- Lower Search Engine Rankings: Since search engines like Google prioritize mobile-friendly websites, not having an optimized site could result in lower ranking in search engine results. That could make it more difficult for customers to find a business’s website.
- Missed Opportunities. An unresponsive website might miss out on potential customers who use mobile devices to search for products or services. Therefore, it could also miss out on potential sales and leads.
- Reduced Conversions: A website that is not optimized for mobile devices will often have a reduced conversion rate since it is more difficult for customers to complete purchases or take desired actions when using a mobile device.
What are some common misconceptions about responsive websites?
There are several misconceptions about responsive websites which sometimes hold keep website owners from designing their website to be responsive or getting it that way once they discover that the website is unresponsive:
- Responsive Websites Require a Separate URL. A common misconception is that a responsive website requires a separate website address or URL. They actually use the same URL as a non-responsive website, but the content and design of the website is displayed differently depending on the device used to view the site.
- Responsive Website Are More Difficult to Build. Another misconception is that responsive websites are harder to build and therefore require more time, effort, and money than a nonresponsive site. A responsive website may require more planning than a standard website, but it’s still a process that can be completed in a reasonable amount of time.
- Responsive Websites Are Not SEO Friendly. As already discussed, responsive websites are actually more SEO friendly because they are favored by Google. Also, they are better than having separate desktop and mobile websites because they have the same content and code which makes them easier for search engine crawlers to index.
- Responsive Websites Load Too Slowly: Responsive websites can be optimized for speed just like any other website. The speed of a website depends on how it is coded and hosted, not on its design.
How can I tell if my website is responsive?
Many website builders, like WordPress, provide tools that will allow you to “see” what a website will look like on a desktop monitor, on a tablet, and over a mobile phone. It may be a good idea to use those tools regularly, particularly when you make changes to a website, to get an idea of what your website looks like on various devices. These tools are not 100% accurate, however. No tools can account for all possible screen sizes or device types nor can they always accurately reflect the performance of a website in an actual environment.
There are other tools available online as well, such as the Website Responsive Testing Tool, that can help you determine if a website is responsive. Tools such as this site will analyze a website and give you a report on its responsiveness. This can be a helpful way to test a website quickly and easily.
The only surefire way to determine whether a website is responsive, however, is to actually look at it on various devices such as a tablet and a mobile phone. If the website looks different on each device, but all of the content is still readable and it’s easy to navigate, then the website is probably responsive.

If I am using a website builder, do I need to worry about my website being responsive?
If you use a website builder, you should still worry and check for website responsiveness, but it may not be as much of a factor as creating a website from scratch. Many popular website builders such as WordPress, Wix, and Squarespace, among others, come with pre-designed templates that are designed to be responsive, but that doesn’t mean they always are. When designing a website, regardless of method of doing so, you may wish to check your website on different devices to ensure that it is truly responsive.
How do I make my website responsive?
- Add the following ‘meta’ tag to your HTML Head:
<meta name=”viewport” content=”width=device-width, initial-scale=1″>
By doing so, you are styling your meta tag as code. - Some markup languages, such as pure HTML, tend to be responsive by nature, but you are very limited to what you can do with just HTML.
- You can use a CSS Flexbox/Grid. CSS dictates how a document looks and controls its responsiveness, and this will allow you to resize items depending on the size of the screen.
- Add breakpoints that will change the design of the website when it starts looking awkward on different sized devices. This includes having a single column of images and text on narrow-screened devices that changes to two or even three columns on wider screens. You can also use a different font size for different break points to increase its readability.
- Set images and other elements to 100vw. By doing so, the elements will be able to resize with the size of the screen.
Matraex is a software and app development company in the northwestern United States. Do you have any app development or technology questions? We would like to provide unbiased answers so you can feel confident making app development or technology-related questions. Feel free to contact us via our website, leave us a note via the live messaging feature on our website, or call us at (208) 344-1115. We look forward to answering all of your questions so you can make informed decisions that are right for you.
Sign up to receive answers to your questions delivered directly to your inbox!
What Is Amazon Web Services (AWS)?

Amazon Web Services, also known as AWS, is a cloud-based computing platform that is owned and operated by Amazon.com. It offers a wide range of tools and services that can help businesses become more agile and increase their innovation.
AWS Services include computation, storage, analytics, networking, and mobile services. AWS is the world’s most popular cloud computing platform with over a million customers in 190 countries. It is used by businesses, from startups to large corporations, organizations, and institutions to build applications.
AWS allows companies to quickly and easily build, manage, and scale applications and services. It can be accessed from anywhere that has internet access. AWS does this by providing needed infrastructure so developers can focus on their projects.
With AWS, developers do not need to worry about storing and analyzing data, how content is going to be delivered, or where they are going to create code. AWS provides flexible and cost effective solutions to these types of problems. This helps companies reduce cost while increasing efficiency.
Why is AWS useful to app developers?
Amazon Web Services is an important tool for developers. It provides a cloud platform that allows them to quickly create reliable and scalable applications. With its wide range of storage, database, and networking services, it allows developers to write code for their applications without worrying about the underlying infrastructure.
It also provides cost-effective, pay as you go pricing. This makes it attractive for developers who want to build applications quickly and cost effectively. It also allows them to scale their applications at a later date.
Why do developers request administrative access to AWS?
Developers request administrative access to Amazon Web Services to facilitate faster development. While the developers are setting up servers, there is often a complex relationship between the numerous resources and services that need to be established and maintained. Allowing administrative access enables developers to set up those relationships between the different systems without needing to communicate why each system is required.
In addition, it may be difficult for an app owner or manager to understand the technicalities involved with AWS and the relationships that needs to be established between different services. It may be simpler, faster, and less confusing to give the developer the access they need. AWS offers foundational services including compute power, network, storage, gateway load balancing, and data warehouse services. AWS offers over 200 total services, which can be overwhelming and confusing.
Administrative access to AWS is also requested so developers can manage advanced security systems. They may also need administrative access so they can monitor and troubleshoot issues when they arise. Without access, they would need to request individual permissions every time something new comes up.
Do developers require administrative access to AWS?
App and software developers may not require administrative access to AWS, but without it, the product owner or product manager may need the knowledge to manipulate some of the AWS services on their own. Without administrative access, the product owner or manager may also need to give multiple permissions for individual access to various AWS tools and services as their app is being developed.
If the developer cannot access to the tools and services they need to implement and integrate into the app and does not give the developer permission, the product owner or manager would need to do it themselves.
What are the most commonly used tools and services of AWS?
The most common features of Amazon Web Services include the following:
- Amazon Elastic Compute Cloud (EC2): A web service that allows users to easily launch and manage virtual machines, or instances, in the cloud. With EC2, users can quickly create a virtual machine and load the machine with their own software. The machine can then be scaled up or down as needed.
- Amazon Elastic Block Storage (EBS): A service that provides secure, high performance storage for Amazon Elastic Compute Cloud (EC2) instances. EBS provides persistent block-level storage volumes that can be attached to and detached from EC2 instances as needed, allowing for dynamic storage to meet application needs.
- Amazon Simple Storage Service (S3): A highly reliable, cost effective storage service that can be used to store data on the cloud. S3 provides a simple web interface for users to store and retrieve any amount of data from anywhere on the web.
- Amazon Relational Database Services (RDS): A managed cloud data service that allows users to quickly launch and manage relational databases in the cloud. Relational databases are organized into tables with rows and columns, and each item on the table is related to one another. RDS is highly scalable and provides many features that help users manage their databases more efficiently.
- Amazon Elastic Load Balancing (ELB): A web service that helps distribute traffic in an application. It automatically routes traffic to multiple instances of the application so they are not all bogged down on one. This provides fault tolerance because it helps to ensure the application is always available to users and can handle incoming requests.
- Amazon CloudFront: A content delivery network(CDN) that helps to deliver content to users around the world. It provides low latency and high transfer speeds.
- Amazon DynamoDB: A NoSQL database service that is highly available, scalable, and secure. A NoSQL database is a non-relational database that stores data in an unstructured way. DynamoDB provides high performance and low latency for applications that need to access large amounts of data.
- Amazon Lambda: A serverless computing service that allows users to run code for applications without needing to manage underlying infrastructure. Lambda is perfect for applications that need to scale quickly and can handle unpredictable workloads.
- Amazon Machine Learning (ML): A service that allows users to easily build, train, and deploy machine learning models in the cloud. This helps to reduce the time and cost associated with building and managing custom machine learning solutions.
- Amazon Redshift: A cloud data warehouse that makes it easy to store and analyze large amounts of data. It is highly scalable and provides a fast, cost-effective way to analyze data.
- Amazon Simple Queue Service (SQS): A message queuing service that helps to manage message-based communication between applications. SQS helps to ensure that messages are delivered in the correct order. It also allows for asynchronous communication between the different components of an application.
- Amazon Simple Notification Service (SNS): A highly scalable push notification service that is easy to set up and operate. It is highly scalable and is a simple and efficient way to fan-out messages to subscribers. SNS allows for notifications to be sent to varying number of recipients with no additional set-up required. It can provide notifications through mobile devices, email, and social media.
Go to “When using AWS, what tools and services are essential for my app?” for specific detail on these and other services.
How does AWS charge for their services?
Matraex is an app development company in Boise, Idaho. Do you have any app development or tech questions? We’d like to be your source for unbiased answers so you be an informed consumer.
Contact Matraex, call us at (208) 344-1115, direct message a question on our website, or put a question on our Google Business Profile. We look forward to talking with you.
Sign up to receive answers to your questions delivered directly to your inbox!
What Is the Difference Between HTTP and HTTPS?

Have you ever noticed, at the beginning of every website URL, are the letters http or https? Take notice and you’ll see that it’s there every time. In actuality, even when you don’t see it, it’s there. But what do http and https stand for? How are they different from each other? And probably most importantly, “Does It Matter?” Yes it does….a great deal. In fact, if you input “http” instead of “https” as the URL, there’s a good chance that the website will not work properly and may not even load at all.
HTTP stands for “HyperText Transfer Protocol”, and it is the protocol used to send data over the internet. Http is written in plain text with no encryption at all. Therefore, http websites can be read by anyone on the internet, even if the page has sensitive or personal information including passwords. The S in https, on the other hand, stands for “secure”. Https websites encrypt all of the data that is sent or received over the internet, which makes it much more secure as well as more difficult to tamper with.
This article will address and provide answers to the following questions:
When were http and https first used?
Http was first released in 1991 by Tim Berners-Lee. Mr. Lee is a British computer scientist who was knighted by Queen Elizabeth II and was named in Time magazine’s 100 Most Important People in the 20th Century edition of December 1999.. And what was Mr. Lee’s claim to fame? He is credited with inventing the World Wide Web. Http was the first interactive text-based web browser and was created alongside HTM, one of the first coding languages, intended for simple text in websites..
Https, on the other hand, was created by Netscape Communications in 1994 as an extension to http to make its web browser, Netscape Navigator, more secure. Its initial purpose was so users could send credit card information securely over the internet to allow for online purchases.
What has https traditionally been used for?
Https has traditionally been used for internet usage that needed to be secure due to the risk of theft or to prevent the release of sensitive user information. Banks, shopping websites, and doctors’ offices/hospitals have used https the longest to make certain that financial or patient information stayed secure.
A little while later, websites started using https to encrypt passwords. In 2008-2009, Microsoft and Google made https optional on their login pages. Within two years, it had become standard for most login pages. Without using https when logging in, your password is in plain text for anyone who chooses to look for it. Over time, https became more mainstream. Now, more than 80% of websites implement https on their websites.
In fact, in 2014, Google turned https into a ranking symbol. They not only started using https in their Google Mail, Google Search, and Google Drive, but also started rewarding sites that followed suit with a higher Google ranking. Therefore, if you wish to rank well on Google, converting your website to https has become essential.
Why is https becoming more important as time passes?
With http written in plain text, it is easy to intercept and use the information contained on http-written websites for malicious purposes. One such purpose is the “the man in the middle” phishing attack. In that attack, the attacker inserts himself into an online conversation, impersonates both parties, and gains information that the two parties were attempting to send to one another without either party’s knowledge. In this manner, the attacker is able to gain access to any sensitive information that they might have been discussing.
Https also reduces the piracy that can occur through an open network connection or public wi-fi network, such as in coffee houses or stores, though it is not fail-safe nor does not stop all attacks from such locales.
What’s more, according to Chris Hoffman, content writer for McAfee in his blog “What is HTTPS, and Why Should I Care?”, internet service providers are legally allowed to spy on their customers’ web browsing history and sell it to advertisers. In matter of fact, Verizon created a supercookie that they are using to track user’s ads. What’s more, documents leaked by Edward Snowden back in 2013 indicated that the U.S. government monitors the internet activity of many users for national security purposes, both domestically and abroad. This activity, which was previously unknown, is controversial and has led to a lot of scrutiny. Using an https URL largely curtails this type of activity. Using Https, however, is not infallible. If you wish to stay secure during your internet usage, you may need to take other steps to protect yourself.
Finally, by using https, you will receive a boost in Google search ranking, so there is a better chance that your website will be found.
How can I distinguish between a HTTP and a HTTPS URL?
It is easy to determine if a website is http or https by a quick visual inspection. By just looking at the website URL, you might be able to figure it out. If it says http, guess what? It’s http – and vice versa. Websites don’t always directly state whether a given website is http or https, however. You can still determine if a website is http or https if you know what to look for. If a website is https, there will be a lock in the upper left-hand corner in front of the URL address such as the following:
What if I open a website using http instead of https?
If you mistakenly open a https website with http, it will more than likely still come up, but some of its functionality may be missing. If the site normally asks for permission to access your location or access to your camera or photos, for example, it probably won’t, nor will the website allow you to do those things. In addition, some pages that request personal or sensitive information may not come up at all. Those pages may appear to have a bug when they are actually functioning according to design since an http website is not secure in any way and would allow for others to see and steal your sensitive information. What appears to be a problem with the site or page, in this case, is actually protecting the user from having personal information stolen.
How do you acquire an https website?
In order to have an https website, a business or organization needs to acquire a security certificate (SSL) which does expire and needs to be renewed. Most SSL certificates need to be renewed every year, though there are exceptions. If the certificate expires, it will cause pages with sensitive information to have issues or, in some cases, not load at all. There are different types of security certificates and there are times, depending on the business or organization, that more than one security certificate may be needed. Some security certificates are very inexpensive, starting at $8 per year, while others can go up to $1000 per year. Types of security certificates include the following:
- Domain Validated (DV) SSL Certificate: This type of certificate validates that the domain name is registered to the applicant through an automated validation process. It does not verify the identity of the organization and does not provide any additional features.
- Organization Validated (OV) SSL Certificate: This type of certificate validates that the domain name is registered to the applicant, and it also verifies the legitimacy of the organization who possesses it. An OV SSL Certificate provides additional features as well such as the company’s name displayed in the certificate.
- Extended Validation (EV) SSL Certificate: This type of certificate provides the highest level of validation available and is used for high-profile, high-security websites. These websites include e-commerce websites, financial institutions, government organizations, and large corporations. It verifies the domain name, the organization, and provides additional features such as a green bar in the address bar.
- Wildcard SSL Certificate: This type of certificate allows a single certificate to be used to secure multiple subdomains of a domain.
- Multi-Domain (SAN) SSL Certificate: This type of certificate allows a single certificate to be used to secure multiple domains.
- Code Signing Certificate: This type of certificate is used to digitally sign software and other code to verify the author and integrity of the code.
Matraex is an app and software development company located in Boise, Idaho, and our goal is to answer all of your app development and tech-related questions so you can be an informed consumer. Have a question? We’d love to hear from you. You can contact us, send us a message through our website, call us directly, or post a question through our Google Business Profile.
Sign up to receive answers to your questions delivered directly to your inbox!
What Is a Cookie and What Does It Do?

It happens all of the time. You visit a new website and the site asks for you to accept cookies. What’s more, in some cases, you can’t proceed to the bulk of the website unless you accept them. Cookies, in this case, are obviously not chocolate chip, but exactly what are they? A cookie is a small text file stored on your computer or mobile device by a website. Cookies are used to store information such as your preferences, login details, and other information that the website may need to personalize your experience. They can also be used to track your activity on a website including what pages you visit and how long you spend on each page.
In article, we will answer the following questions:
Why do websites ask for consent for cookies?
There are several laws that require consent for cookies since the websites are collecting private information. The California Consumer Privacy Act (CCPA) requires websites to explicitly ask for user consent before collecting personal data from visitors. This includes cookies. The website must also provide an obvious link to a page that explains what data is collected and how it is used and shared as well as how to opt out of data collection. The European Union’s General Data Protection Regulation also requires user consent of cookies.
Should I allow cookies?
Whether or not you accept cookies depends on the purpose of the cookies and the website itself. Generally, it is safe to accept cookies, but if you are worried about the website that is collecting the data, it might be best to check the website’s privacy policy before accepting.
What benefits do cookies have?
Website cookies can have several advantages:
- Cookies can improve user experience because they store user preferences and session information.
- Cookies enhance web performance because they provide information that can be used to optimize the web page content.
- Cookies allow users to be authenticated and tracked, which can improve website security.
- Cookies provide advertisers with information about a user’s browsing habits so they can target ads more effectively.
- Cookies can increase and improve the functionality of a website by storing information for shopping carts and user accounts.
What are the disadvantages of cookies?
Cookies also have some disadvantages:
- While they can potentially make a website more secure, they are not secure for the user. They are essentially text files that can be read, copied, and even modified by anyone with access to a user’s computer. Therefore, they can pose a security risk for the user.
- Cookies can track user activity and store information, which can be a privacy concern.
- Cookies can be large in size and potentially slow down the loading time of a web page.
Why should I consider deleting cookies?
Cookies can contain a lot of personal information including what websites you’ve visited and login details. This data can be used to track your activity, target you with ads, and exploit your information without your knowledge, sometimes for malicious intent. Deleting cookies can reduce the risk of this happening.
Also, cookies can take up space on your computer. Deleting them can help to free up space and declutter your computer which might allow your computer to run smoother.
Matraex is an app and software development company which is based in Boise, Idaho. Do you have any app development or tech questions? We’d like to be your source for answers. Contact Matraex, call us at (208) 344-1115, direct message a question on our website, or put a question on our Google Business Profile. We look forward to talking with you.
Sign up to receive answers to your questions delivered directly to your inbox!
What Is Artificial Intelligence (AI)?

Artificial Intelligence (also known as AI) is a branch of computer science that focuses on developing computer systems that have the ability to think, work, and react like humans and to perform tasks that normally require human intelligence. This involves accurately and efficiently processing large amounts of data and making decisions or predictions based on that data. AI can also be used to create self-learning systems that can learn from data and improve their performance over time, and more and more businesses are using AI as a way to streamline their operations. Let’s discuss and give some examples of how AI is currently being used. Keep in mind that these examples of AI are only a few of its many uses. These uses also often overlap in one app or piece of technology.
In this article, we will be covering the following types of artificial intelligence:
Image Recognition
Image recognition is a process in which a computer system is able to recognize and identify objects. These objects include people, places, writing, and actions in both still images and videos. With image recognition, a user can take a picture of an object, and AI will tell them who or what the object is. Google Lens, CamFind, and Amazon Rekognition are apps that currently use image recognition technology. While this can be used to benefit the user, in some cases, apps can use AI with user photos in ways their users may not expect. Benefits, unfortunately, sometimes come with negative consequences as well.
Natural Language Processing and Speech Recognition
Natural language processing and speech recognition work hand-in-hand to enable machines to understand, interpret, and generate human language. These technologies are integrated in many home devices that allow you to talk to the machine to turn on your lights and other appliances in your home without lifting a finger and to use Siri or Cortana to answer questions and fulfill requests. Natural language processing and speech recognition are also used in automated customer service and dictation software.
Autonomous Navigation
Autonomous navigation enables vehicles to move from place to place without human intervention. Such systems use sensors, cameras, and mapping data to navigate the environment. In addition, they are often programmed to react to changes such as traffic and road conditions. Autonomous navigation is used in self-driving cars, robots, and drones.
Machine Learning
Machine Learning uses algorithms that enable a machine to learn from provided data and make predictions based on that data. In this manner, systems access data and use it to automatically learn and improve without being explicitly programmed. One app that uses machine learning is Netflix. Netflix recommends content based on the content the user already watched through machine learning. Netflix also uses it to identify and block fraudulent accounts, to detect and reduce piracy, and to target potential customers with personalized ads.
Predictive Analysis
Predictive analysis uses data mining and statistical analysis to identify patterns and trends in data and then to predict future outcomes and behaviors. It can be used to make predictions about customer behavior and market trends. It can also be used to predict the success of a product or service, the likelihood of an event occurring, or the outcome of a particular decision. Weather apps use predictive analysis for more accurate forecasting, financial apps for identifying trends in the market and offering investment advice, and healthcare apps for identifying health risks and suggesting preventive measures.
Robotics
Robotics is a branch of technology that deals with the design, construction, operation, and use of robots as well as computer systems for their control, sensory feedback, and information processing. These technologies are used to develop machines that can substitute for humans and replicate human actions. Starship Technologies is a mobile app that allows users to order food and other items which are then delivered by robots.
Decision Making
During the decision making process, a machine makes a choice between two or more alternatives. It involves gathering information and assessing the available options to make the best decision. Shopping apps like Amazon, Ebay, and Wish use decision making to make personalized product recommendations to customers and to suggest alternatives if the user’s first choice is not available. Health and fitness apps such as MyFitnessPal and Fitbit also use decision making to track and analyze user activity and dietary habits. They then suggest personalized plans to help the user reach their health and fitness goals.
Artificial Intelligence is still an emerging technology, and we’ve only touched the surface of what might eventually be possible. It has and will continue to change how we interact with the physical world, to take over mundane tasks, to optimize operations in many fields, and to help us make better decisions.
Matraex is a premier software and app development company based in Boise, Idaho. Do you have any questions regarding app development? Matraex would like to become your go-to source for answers so you can be an informed consumer. Feel free to contact us, call us at (208) 344-1115, send us a message on our website, or post a question on our Google Business Profile. We’d love to hear from you.
Sign up to receive answers to your questions delivered directly to your inbox!