SMTP on AWS SES – Limit IP Addresses – Best Practice (Original)
If you are here – it is likely because your SMTP Credentials have already be compromised and you dont want it to happen again, or you have excellent instincts and are planning ahead.
Below you will see how to limit your SMTP Credentials on SES to only your IP Addresses.
Of course follow the basics of credentials and passwords
- Un guessable
- Dont reuse
- Dont share
- Rotate
When it comes to AWS – SES SMTP Credentials – the ones often used in code and programmatically – the thought may be to set it and forget it. Here is a best practice in those situations to only allow sending from your networks and futher lock down the use of these (or any other) IAM SMTP users.
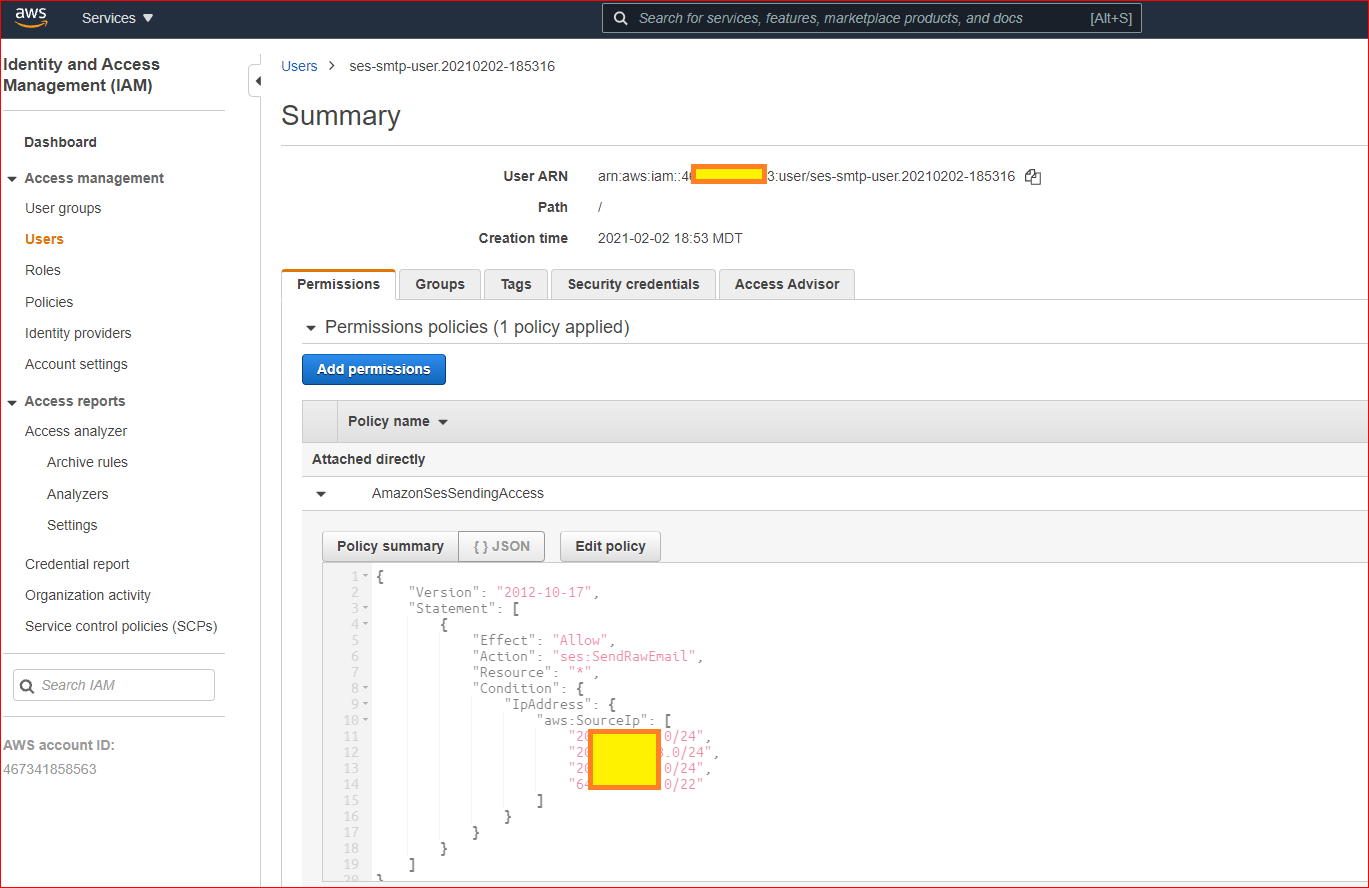
Setup an IPAddress Condition which restricts sending to only your Allowed IP Address(es)
Here is how to do it in the AWS Console
- Goto IAM > Users
- Select [user]
- Go to the Permissions tab
- click the arrow to expand the AmazonSesSendingAccess
- Click Edit Policy
- Update the JSON to add the Condition:IPAddress (below) for the IP Addresses you want to restrict to
Here is an example of my full policy with multiple allowed IP Addresses.
{
“Version”: “2012-10-17”
“Statement”: [
{
“Effect”: “Allow”,
“Action”: “ses:SendRawEmail”,
“Resource”: “*”,
“Condition”: {
“IpAddress”: {
“aws:SourceIp”: [
“xx.yy.zz.0/24”,
“xx.zz.yy.0/22”
]
}
}
}
]
}
Here is a screen shot to help show exactly what it looks like in the AWS Console as it is now.
So then, go do it! https://console.aws.amazon.com/iam/home
This condition can be applied to many of your other IAM users too.
Sign up to receive answers to your questions delivered directly to your inbox!
